Articles
Welcome to our articles page. You will find articles on various aspects of Information Security and Business Continuity promulgated here. This is done on an ongoing basis for free of cost for your education. We emphasize your cooperation to refrain from redistributing our content for commercial purposes without our prior written consent. However, you are free to use it for your personal (educational and research) purposes or to implement a certain roadmap or strategy in your organization.
We partner with CyAlpha — a Calgary-based Cyber consulting firm, to offer you the above services.
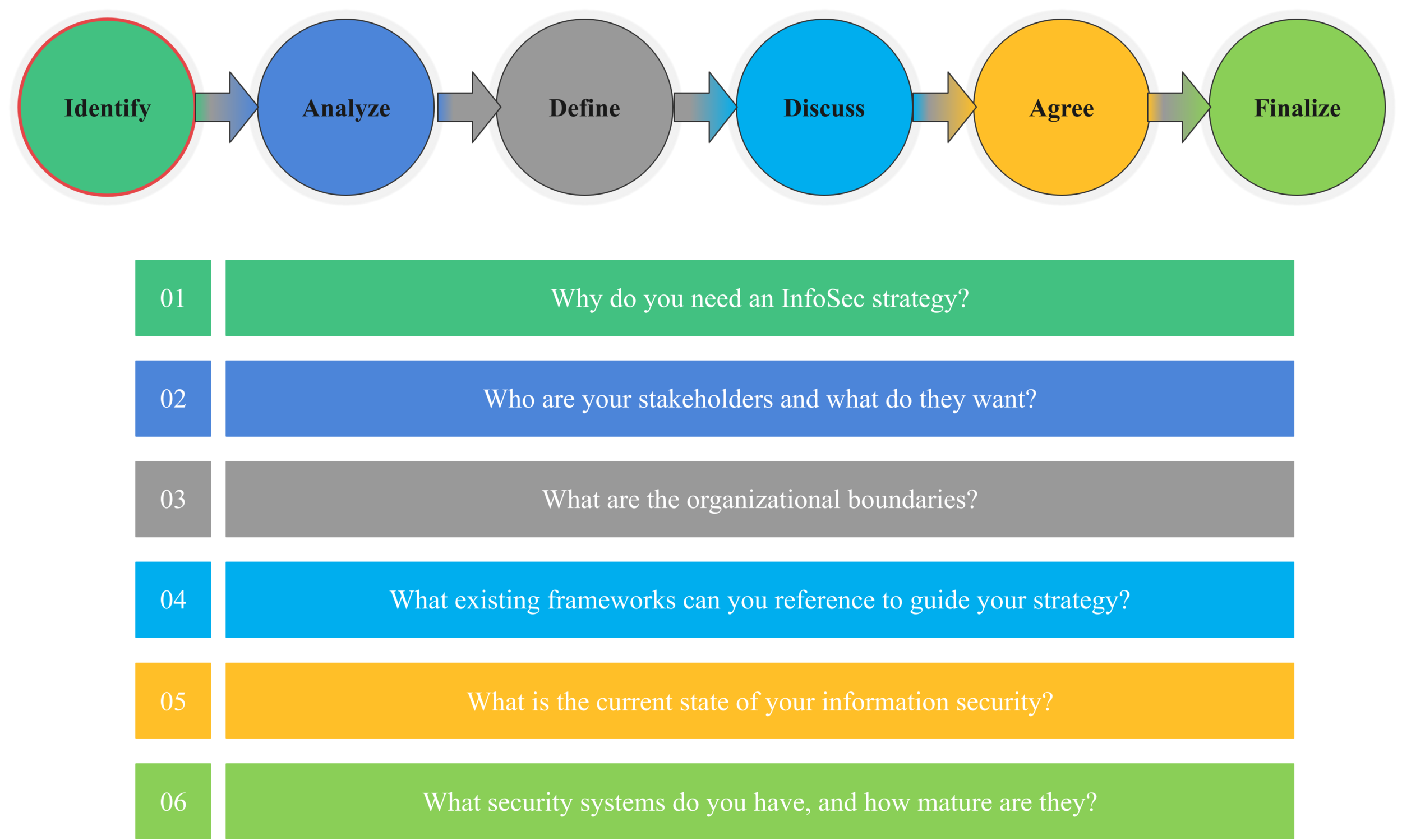
Developing Information Security Strategy: Concluding IDENTIFY phase
Continuing where we left in the previous article, in this article, we discuss the last four activities involved in the IDENTIFY phase, that is organizational boundaries, security frameworks, how to assess the current state of the previous security programs, and finally, how to assess the maturity of the security systems that are already in place.
Developing Information Security Strategy: Planning for stakeholder requirements
In this article, you will learn about profile canvas templates and how to integrate them into a workshop setting. Developing hypothetical stakeholder profiles before the workshop can help you figure out the direction the interviews should take. Customer profile canvas lets you learn more about the expectations of the business from the Cybersecurity strategy.