Articles
Welcome to our articles page. You will find articles on various aspects of Information Security and Business Continuity promulgated here. This is done on an ongoing basis for free of cost for your education. We emphasize your cooperation to refrain from redistributing our content for commercial purposes without our prior written consent. However, you are free to use it for your personal (educational and research) purposes or to implement a certain roadmap or strategy in your organization.
We partner with CyAlpha — a Calgary-based Cyber consulting firm, to offer you the above services.
Business Continuity Planning: Conducting the risk assessment and reporting
Once your team has prepared for the risk assessment phase, you should identify the risks to the key processes (and their dependencies, including manpower, office, information and hardware). Once identified, these risks should be analyzed and ultimately their severity and likelihood should be evaluated. These findings should then be discussed with enterprise risk teams, GRC, department heads, presented to the applicable committee(s) and transferred to your enterprise risk management team for tracking.
Business continuity planning: Preparing to conduct the risk assessment
Once the business impact reporting is done, preparation to conduct risk assessment must commence. The scope and context for the risk assessment must be defined and the analysts must be identified. A framework to conduct the risk assessment must be developed or adopted, depending on the availability of such a framework in your organization. Then you need to conduct a workshop with the risk management team to discuss your plan, incorporate their feedback and then present the strategy for this phase of the program to the committee and the champions.
Business continuity planning: BIA Analysis and reporting
In this article, we will look at the post-interview analysis, clarifications stage and the process for reporting and acceptance.
Business continuity planning: Conducting the Business impact analysis interviews
In Part 6 of our Business Continuity Planning series, we discussed the preparations required to conduct interviews for a business impact analysis (BIA). In this article we will discuss conducting interviews with your selected champions and subject matter experts (SMEs) for the analysis.
Business continuity planning: Preparing for the Business impact analysis
Business impact analysis is a crucial part in planning for business continuity, so designing a thorough data collection template is essential. The template must be designed according to your company needs and then tested with some real business scenarios. Only then, can you confirm the interview schedules and officially begin conducting your analysis. In this article, we will discuss preparing for business impact analysis which is part of the planning stage of the program.
Business continuity planning: program planning
So far in our Business Continuity series, we have discussed the many benefits of having a plan. We’ve also outlined some of the key stakeholders that serve as the building blocks for a successful continuity program. Once a program is underway, there are several planning aspects to consider. In this article, we will outline some of them, so that your organization can have a successful planning phase.
Business continuity planning: requirements, scope of work and deliverables
So far in our Business Continuity series, we’ve outlined why continuity plans are important, the various stakeholders that should be consulted and additional factors like geographically distributed operations that should be considered. In this article, we will discuss the importance of defining the scope of your organization’s continuity plan and the steps we recommend when proposing the scope to management.
Security Data Analytics and Reporting, Developing reporting viewpoints: CISO
The security reporting viewpoint used by CISOs consists of views such as the state of security compliance, security posture and cybersecurity trends. These views must be meaningful to the CISO and thereby help them make decisions that retain or improve organizational cybersecurity posture. This also helps the CISO demonstrate the effectiveness of the organization's security investments to the board of directors (or whoever they’re reporting to).
Security Data Analytics and Reporting, Developing reporting viewpoints: Board of Directors
A Viewpoint is an architectural term in the Information Technology world that is used to describe the stakeholders and their concerns for constructing organizational views on technology. In the case of SDAR, a viewpoint is a reporting view for an organization’s stakeholders, based on their stakeholders’ concerns. This article discusses the viewpoint of the Board of Directors using Akrogoniaios Technologies Corp as publicly listed consumer SaaS product company.
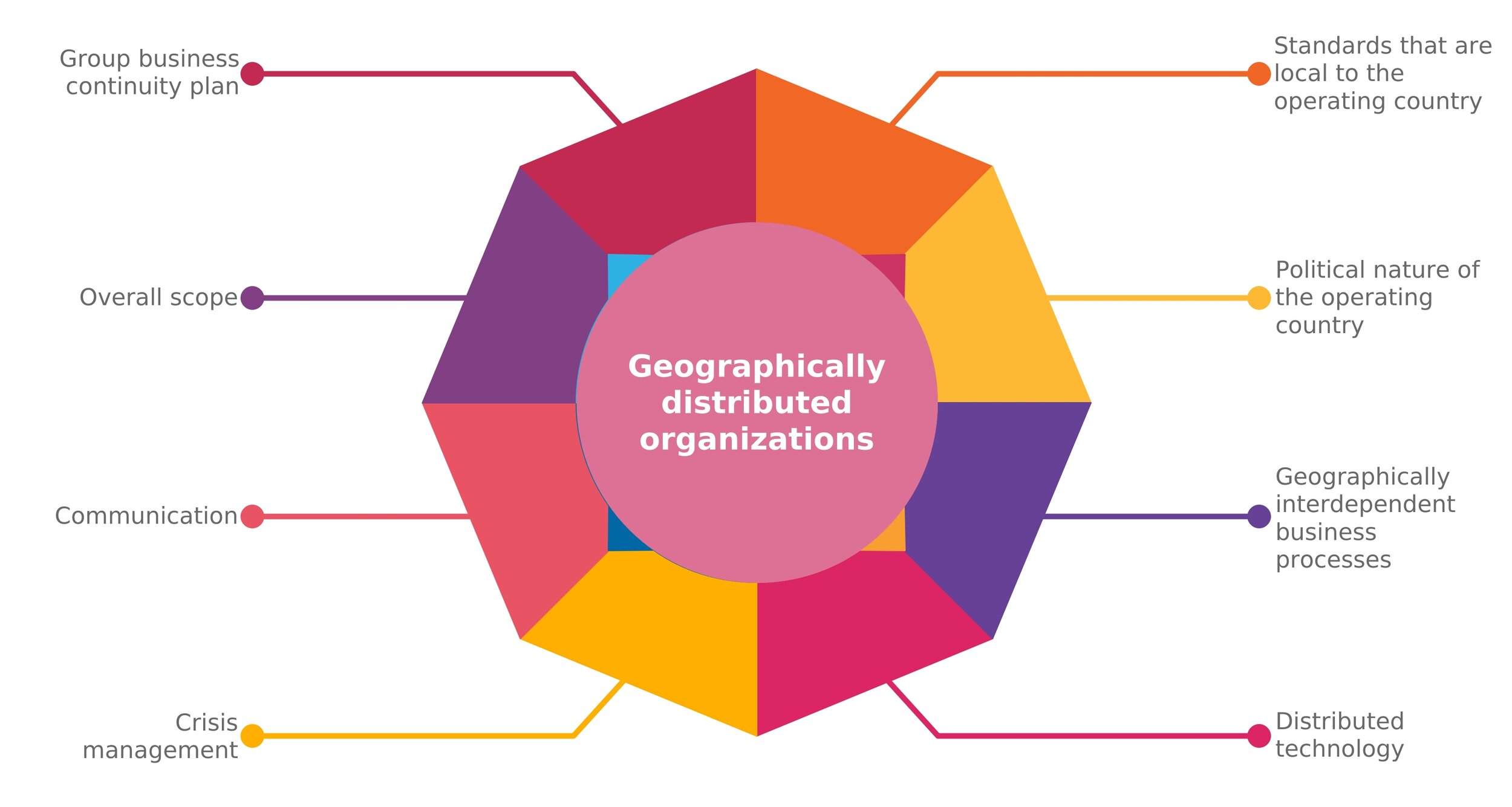
Building Blocks: Geographically Distributed Organizations
Building blocks: stakeholders and drivers was an overview of the various stakeholders that an organization should consider when developing a business continuity plan. The article also outlined some of the common drivers for continuity plans.This article will discuss another factor that influences business continuity plans: geography.