Articles
Welcome to our articles page. You will find articles on various aspects of Information Security and Business Continuity promulgated here. This is done on an ongoing basis for free of cost for your education. We emphasize your cooperation to refrain from redistributing our content for commercial purposes without our prior written consent. However, you are free to use it for your personal (educational and research) purposes or to implement a certain roadmap or strategy in your organization.
We partner with CyAlpha — a Calgary-based Cyber consulting firm, to offer you the above services.
Developing Information Security Strategy: Define your solutions
In the previous article, we discussed the ANALYZE phase. The purpose of the ANALYZE phase is to determine the context for your security strategy, identify the problem statements from each stakeholder, and list your organization’s problem patterns.
This article will discuss the DEFINE phase of our seven-step design thinking process for developing an InfoSec strategy. The goal is to define your Infosec solutions for the requirements you have identified in the previous phase.
Developing Information Security Strategy: Conducting the analysis
In this article, we will outline the next step: the ANALYZE phase.
The goals of the ANALYZE phase are to:
Consolidate information from the IDENTIFY phase
Begin defining the InfoSec program objectives
Describe the problem statements,
Identify problem patterns
Gain sufficient insight to define the strategy
This helps us analyze the information we have gathered to gain enough insight to define our InfoSec strategy.
Developing Information Security Strategy: Concluding IDENTIFY phase
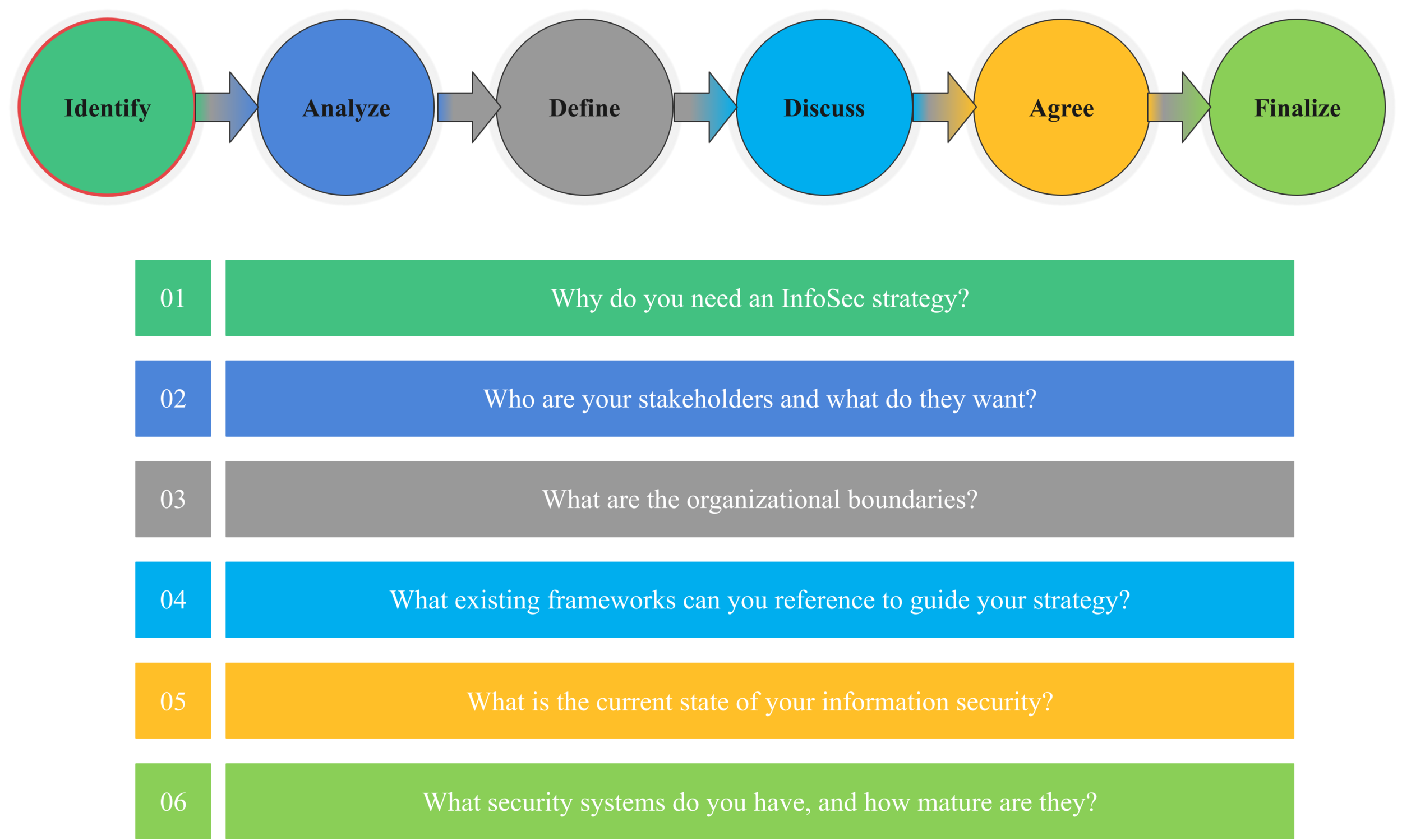
Continuing where we left in the previous article, in this article, we discuss the last four activities involved in the IDENTIFY phase, that is organizational boundaries, security frameworks, how to assess the current state of the previous security programs, and finally, how to assess the maturity of the security systems that are already in place.
Developing Information Security Strategy: Conducting workshops and interviews
In this article, we continued discussing the workshop stage and outlined how to conduct interviews. We also discussed the importance of the trigger questions and gave you some sample outcomes for the customer jobs, pains and gains. In the next article, we will conclude the Identify phase by discussing the other aspects that are important to move to the next phase.
Developing Information Security Strategy: Planning for stakeholder requirements
In this article, you will learn about profile canvas templates and how to integrate them into a workshop setting. Developing hypothetical stakeholder profiles before the workshop can help you figure out the direction the interviews should take. Customer profile canvas lets you learn more about the expectations of the business from the Cybersecurity strategy.
Developing Information Security Strategy: Introduction
This is the first of a new multipart educational series: Developing Information Security Strategy.
Organizations sometimes build walled gardens to secure information — a heavily armed ecosystem that does not interact freely with the outside world to support ideas that can push the company forward.
We have used Design Thinking process to radically rethink the way we design and implement InfoSec Strategy in the organizations.
This is not yet another framework such as COBIT to implement your InfoSec strategy. Instead, this is a method to design your InfoSec strategy that benefits your organization and receive support from your peers.
In this series, we will explore a range of topics that are necessary to create an optimal strategy, including:
How to incorporate security operations into your strategy
Information classification
How to integrate SIEM, SOAR and SDAR
When to outsource some or all of of your InfoSec strategy
Business Continuity Planning: Testing, documenting and operationalizing
In Part 13 of our Business Continuity Planning series, we discussed how to design a business recovery strategy. This article will cover the final stages of building a BCP. You will learn:
how to conduct awareness workshops
how to test your recovery strategy
how to document your BCP how to operationalize your BCP
Business Continuity Planning: Components of the recovery strategy
In Part 12 of our Business Continuity Planning series, we discussed the key inputs you need to define your organization’s recovery strategy, as well as the advantages of having a secondary physical location that can be used as a recovery site. In this article, we will discuss the components of the recovery strategy that are necessary to document and operationalize.
Business Continuity Planning: Requirements to design a recovery strategy
In Part 11 of our Business Continuity Planning series, we discussed some of the key aspects of building a recovery strategy, such as disaster categorization and classification. In this article, we will discuss what you should consider when designing your recovery strategy.
Business Continuity Planning: Preparing to draft the recovery strategy
A well executed recovery strategy could mean the difference between your organization bouncing back after a disaster or never recovering. While there are countless potential disasters you can face, if you can categorize them into two or three simple groups and assess the severity of the risks, you will find it much easier to respond quickly and effectively when something does happen.