Articles
Welcome to our articles page. You will find articles on various aspects of Information Security and Business Continuity promulgated here. This is done on an ongoing basis for free of cost for your education. We emphasize your cooperation to refrain from redistributing our content for commercial purposes without our prior written consent. However, you are free to use it for your personal (educational and research) purposes or to implement a certain roadmap or strategy in your organization.
We partner with CyAlpha — a Calgary-based Cyber consulting firm, to offer you the above services.
Security Data Analytics and Reporting, Developing reporting viewpoints: Board of Directors
A Viewpoint is an architectural term in the Information Technology world that is used to describe the stakeholders and their concerns for constructing organizational views on technology. In the case of SDAR, a viewpoint is a reporting view for an organization’s stakeholders, based on their stakeholders’ concerns. This article discusses the viewpoint of the Board of Directors using Akrogoniaios Technologies Corp as publicly listed consumer SaaS product company.
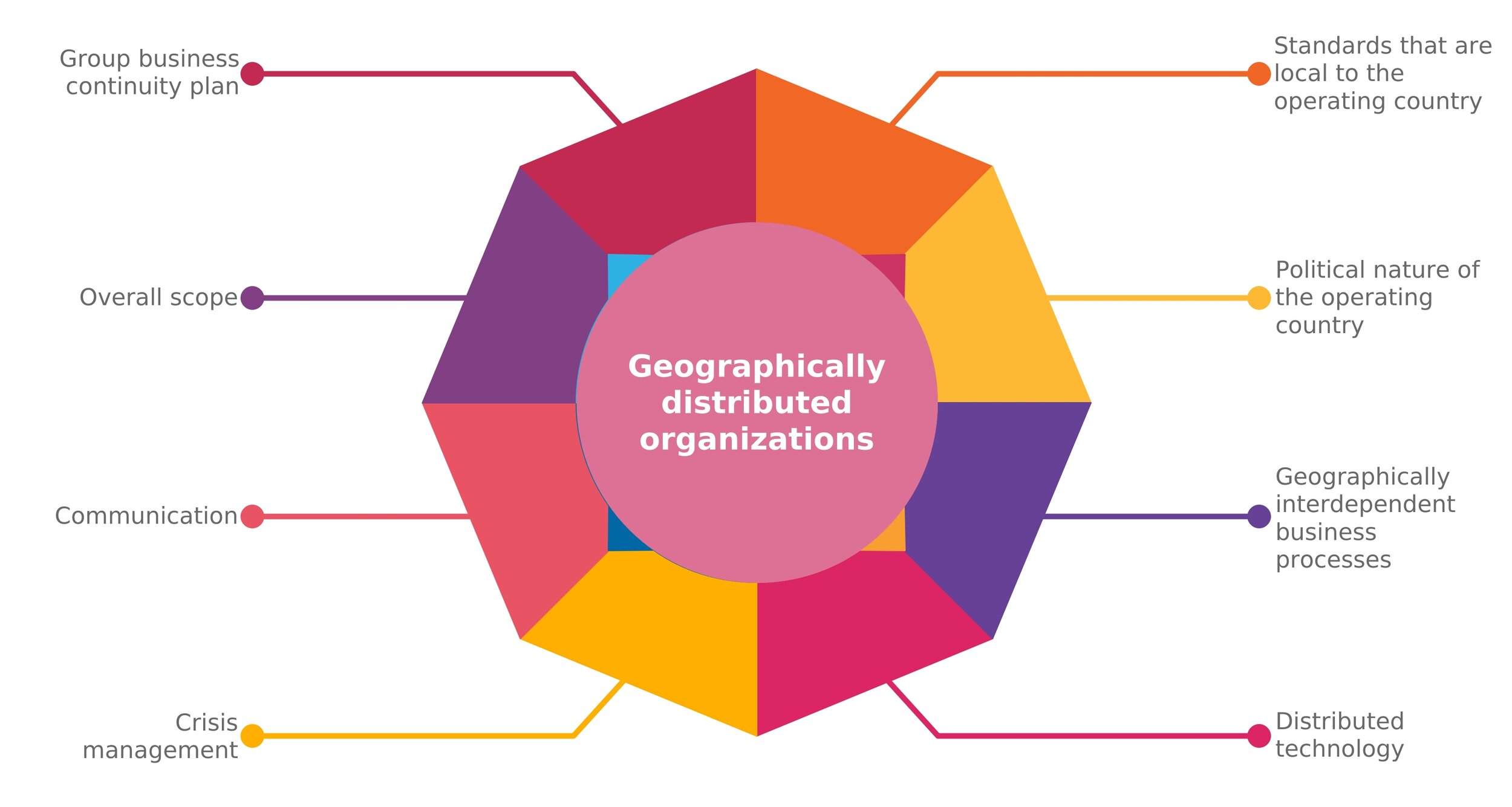
Building Blocks: Geographically Distributed Organizations
Building blocks: stakeholders and drivers was an overview of the various stakeholders that an organization should consider when developing a business continuity plan. The article also outlined some of the common drivers for continuity plans.This article will discuss another factor that influences business continuity plans: geography.
Security Data Analytics and Reporting: Business Expectations and value - Part 2
Businesses expect their information security systems to provide security assurance. To some extent, businesses understand what successful security looks like. However, to prove that the investments into security programs are effective, stakeholders must feel the reports are relevant. When security teams take the above steps, they ensure that the organization has maximum visibility. The backbone in providing such reporting is Security Data Analytics and Reporting (SDAR).
Building Blocks: Stakeholders and Drivers
Stakeholders and the extent of their need for a business continuity plan depends on their ownership type and industry. In all scenarios, It is important to understand stakeholders that have an interest in the survivability of the business. Once that is understood, the key business drivers can be developed with inputs from the right stakeholders.
Security Data Analytics and Reporting: Monitoring and reporting domains
Segregating reporting into domains helps organizations design reporting suited to each of recipients. In this article, we looked at the physical, logical and management domains at a high level. Future articles will detail the reporting viewpoints and then map stakeholders and their requirements with the reporting domains to design and deliver an SDAR system.
Security Data Analytics and Reporting: Organizational requirements
Reporting expectatoin varies depending on the owership and industry of an organization. This article will focus on how SDAR expectations and requirements differ, based on organizational type.
Security Data Analytics and Reporting: Stakeholders
The first step a business must take when implementing SDAR is to identify who its stakeholders are. Next, the business should analyze their stakeholders’ high level requirements, technology domains and viewpoints. Finally, the business can tie all this together and implement SDAR.
This article will explore the different types of stakeholders an organization can have and their respective responsibilities.
SIEM, SOAR and SDAR
SDAR is quite robust and can be a useful cybersecurity tool, even without accompanying SIEM and SOAR systems.
Business continuity planning: overview
Every organization must give some thought into creating a business continuity plan, but plans should be realistic and flexible — not perfect. To create an effective continuity plan, businesses must consider organizational strategy, context, stakeholders, technology, geographical location, appetite for developing a plan, benefits, and the challenges they might face.
SIEM, SOAR and SDAR
This article will give you a high-level overview of the different terminologies and overlapping features of some common IT tools. You’ll also learn, in detail, about SIEM software and its use cases. Please refer to the glossary page for all the acronyms and definitions used in this article.